Introduction
Google Play Music Desktop Player (GPMDP) is an amazing application. Instead of opening up a browser every time to access your Google Music account (and songs), you can integrate it into your desktop experience instead. One of the best features GPMDP offers is the fact it becomes a standalone application and no longer requires you to have to deal with the memory hogging web browsers (especially Chrome) uses to stream your favorite music!
GPMDP doesn’t stop there though, there are tons of great features it offers that extend the already great functionality Google Music offers! Just to quote directly from their README file:
- Supports media keys (play, pause, stop, next, previous)
- last.fm Scrobbling and Now Playing support!
- Hands free Voice Controls!
- Desktop notifications on track change
- A simplistic mini player
- Customizable Dark theme
- Smooth scrolling and overlay scrollbars for a nicer user experience.
- HTML5 Audio Support – No more Adobe Flash Player!
- Minimize to task bar for background music playing
- Customizable hotkeys for those who don’t have media keys.
- Choose your audio output device from within the player.
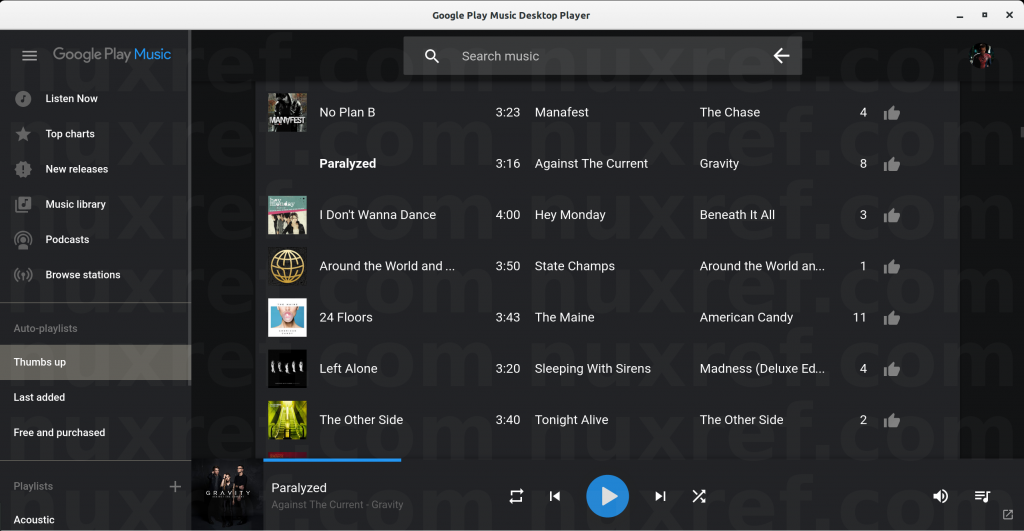
I set up this blog because the RPMs distributed from GPMDP’s official website didn’t work for me. So I just ended up repackaging the whole thing and thought I would share my success.
It’s also important to note that this blog assumes you have a subscription to Google Music. If you don’t have one (and don’t intend to get one), then there is no need to read any further. 🙂
Installation
If you are hooked up to my repository, you can upgrade to the latest packages through the following simple command:
- CentOS (or Red Hat) 7.x:
# Run as root (or a user with sudoers permission) sudo yum -y install --enablrepo=nuxref google-play-music-desktop-player # Or you can do it manually: # I sign everything; so it wouldn't hurt to just grab my key rpm --import http://repo.nuxref.com/pub/NUXREF-GPG-KEY # Now you can install the player rpm -Uhi http://repo.nuxref.com/centos/7/en/x86_64/custom/google-play-music-desktop-player-3.2.1-1.el7.nuxref.x86_64.rpm
- Fedora 22:
# I sign everything; so it wouldn't hurt to just grab my key rpm --import http://repo.nuxref.com/pub/NUXREF-GPG-KEY # Now you can install the player rpm -Uhi http://repo.nuxref.com/fedora/fc22/en/x86_64/custom/google-play-music-desktop-player-3.2.1-1.fc22.nuxref.x86_64.rpm
- Fedora 23:
# I sign everything; so it wouldn't hurt to just grab my key rpm --import http://repo.nuxref.com/pub/NUXREF-GPG-KEY # Now you can install the player rpm -Uhi http://repo.nuxref.com/fedora/fc23/en/x86_64/custom/google-play-music-desktop-player-3.2.1-1.fc23.nuxref.x86_64.rpm
- Fedora 24:
# I sign everything; so it wouldn't hurt to just grab my key rpm --import http://repo.nuxref.com/pub/NUXREF-GPG-KEY # Now you can install the player rpm -Uhi http://repo.nuxref.com/fedora/fc24/en/x86_64/custom/google-play-music-desktop-player-3.2.1-1.fc24.nuxref.x86_64.rpm
- Fedora 25:
# I sign everything; so it wouldn't hurt to just grab my key rpm --import http://repo.nuxref.com/pub/NUXREF-GPG-KEY # Now you can install the player rpm -Uhi http://repo.nuxref.com/fedora/fc25/en/x86_64/custom/google-play-music-desktop-player-3.2.1-1.fc25.nuxref.x86_64.rpm
Gnome Media Player Shell Extension
Pair this application with the Gnome Media Player Shell Extension and you’ll allow even get desktop notifications when songs change.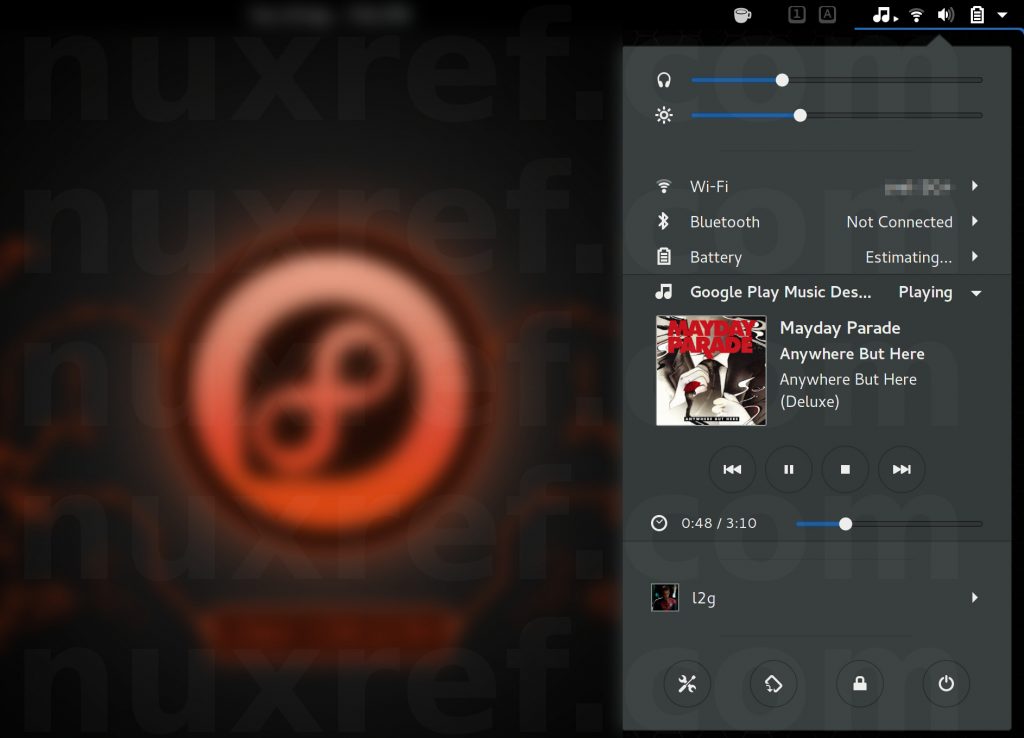
For CentOS / Red Hat 7 users, this extension sometimes does not properly install itself. So to make your life easier, I went ahead and packaged it into it’s own RPM as well. You can install it like so:
# Assuming you're hooked up to my repository, you can # just easily install it: sudo yum install --enablerepo=nuxref gnome-shell-extension-mediaplayer
I didn’t forget about the Fedora users either. It’s also in the repository (if you’re hooked up):
# Assuming you're hooked up to my repository, you can # just easily install it: sudo dnf install --enablerepo=nuxref gnome-shell-extension-mediaplayer
RPMs
You can also just visit the locations where I posted these RPMs and fetch them manually:
| Google Play Music Desktop Player | Gnome Media Player Shell Extension | |
|---|---|---|
| CentOS/Red Hat 7.x | rpm / src | rpm / src |
| Fedora 22 | rpm / src | rpm / src |
| Fedora 23 | rpm / src | rpm / src |
| Fedora 24 | rpm / src | rpm / src |
| Fedora 25 | rpm / src | rpm / src |
Credit
All of the custom packaging in this blog was done by me personally. I took the open source available to me and rebuilt it to make it an easier solution and decided to share it. If you like what you see and wish to copy and paste this HOWTO, please reference back to this blog post at the very least. It’s really all I ask.
Sources
- Google Play Music Desktop Player Official website and GitHub Page.
- Gnome Shell Media Extension and GitHub Page.


